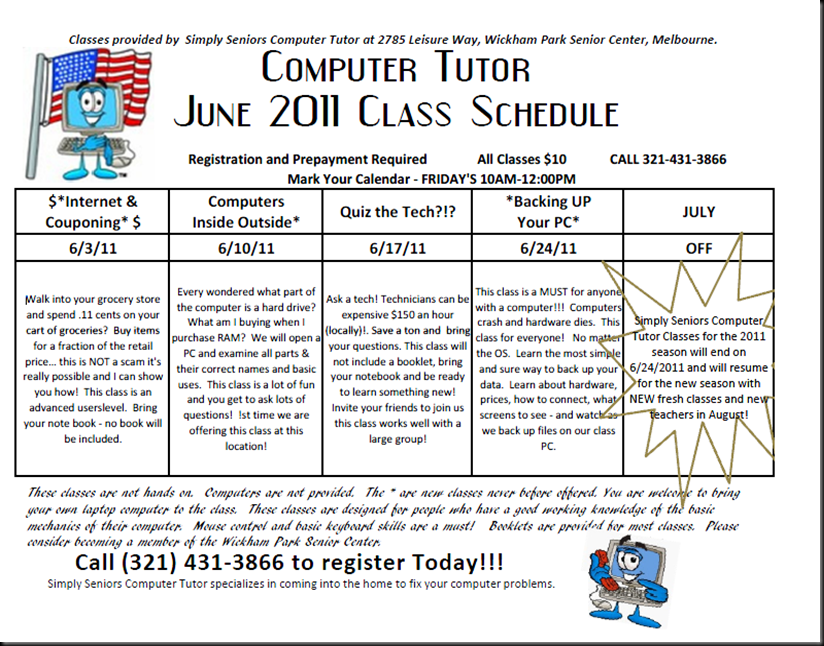
Simply seniors Computer Tutor loves showing people new things! Many of our seniors are now using Facebook on a daily bases and some even Tweet! Today we are going to look at the basics to creating a Twitter account, then we will review article on how to create the type of Tweets people want to read and share with their followers ie., (friends, social network). Lastly, we will find out what methods one can use to bring the followers to your account.
How to create a Twitter account from www.ehow.com:

Twitter is a social networking/blogging site that allows you to update your personal blog and communicate with your online friends via 140-maximum character messages, or "tweets," that describe your current status. Whether you are reading something online, or boarding a plane, Twitter is a great way to keep in touch.
- Go to The Twitter homepage and scroll all the way to the bottom. Click on the "Get Started" button.
- Create a username and password. Twitter will automatically check the availability of your username. Once you find one that is unique, enter your email address and continue.
- After you create your account, you can manually see if any of your e-mail contacts are on Twitter. Just enter your e-mail username and password, and twitter will automatically import anyone it recognizes.
- Invite friends. Any emails Twitter didn't recognize, it will display on the next page. You will be able to check different email addresses to send invites to.
- Search for friends. Chances are good that your friends have multiple email addresses, so it is a good idea to enter their name in the search bar and double check.
- Set up your phone. The big advantage of Twitter is that you can update via text messages from your phone. Go to the "Devices" tab on your profile page and then enter your cell phone number. A confirmation message will be sent to your phone, and then you'll be able to make your first update.
Read more: How to Create a Twitter Account | eHow.com http://www.ehow.com/how_4541204_create-twitter-account.html#ixzz1GoZawhMU\
-----------------
A new service being offered by Computer Tutor Consulting, is our “Be Socially Challenged NO MORE” package. We will set up any 3 of your Twitter, Facebook, Linked In, Google Buzz, Yahoo, AIM, Windows Live, Skype, Blogger, and link these accounts for just $99 set up fee! In addition get a 6month maintenance package for just $59 month for the 1st 6 months! This is a deal that will pay for itself in publicity in NO time flat! Call 321-431-3866 Today! Ask about the Socially Challenged Package!
---------------------
Writing the perfect tweet; this was written by and published at http://twittercism.com/the-perfect-tweet/
How To Write The Perfect Tweet
Tuesday, March 9th, 2010 at 8:00 am
Share28
Twitter has rapidly become the ultimate platform for sharing and exchanging link content. For bloggers and brands, Twitter has surpassed Digg, Stumbleupon, Delicious and Reddit as the greatest and most efficient way to build website traffic.
 Better still, by building an engaged andrelevant community, marketers can continue to reap the benefits of that traffic on a daily basis. Almost by accident, Twitter has provided us with a new and improved take on permissive marketing, which has allowed the network to leave many other websites in its dust.
Better still, by building an engaged andrelevant community, marketers can continue to reap the benefits of that traffic on a daily basis. Almost by accident, Twitter has provided us with a new and improved take on permissive marketing, which has allowed the network to leave many other websites in its dust.
It’s not all gravy, though – it’s easy to make mistakes that can be very costly indeed, leaving your tweet (and content) all but ignored. Continue making those errors, and Twitter will be about as beneficial to your brand and website as a badly-drawn flyer at your local community centre.
And while it’s perfectly acceptable to link to your own content, if you over-sell it, self-promote too much, or start to resemble an old-fashioned salesman (even slightly), you’re very quickly going to be overlooked. Worse, likely it won’t be too long before you’re labelled as nothing more than a spammer.
When you get right down to the nitty-gritty, only two things really count when striving for the perfect tweet:
- Maximum readability
- Maximum retweetability
These are both vital, but neither should be tailored at the expense of the other. For maximum benefit, each needs to be perfect every single time.
1. Think Like Your Readers
This is a bit of a no-brainer, but it’s easily overlooked. For your tweet to be perfect, it needs to appeal most to your readers, to the majority of your network, and not to you.
Unless you’re a world-famous celebrity or brand with millions of devoted followers, adopting an attitude of ‘they’ll know what I mean’ will almost always backfire.
You have to take the time to craft your tweet accurately and pleasingly, thus ensuring that it will be appeal to the highest number of readers.
2. Use Consistent Excellence To Stand Out From The Crowd
Take a moment to peruse your Twitter feed. Refresh the page. Who stands out? Why?
Through prolonged Twitter use we all become tuned into paying attention to certain things in our timelines, notably the avatars and usernames of our favourite profiles. But a friend or valued associate sharing new content isn’t always enough to make us click on that link. We trust their judgement, and we have liked some of the things they’ve shared in the past, but this hasn’t turned us into a robot, automatically clicking on everything they tweet.
Conversely, there are many times when we suddenly notice the tweet of somebody we’ve only recently started following, or have previously not paid much attention to, because it was excellent. It ticked all of our boxes, and we read the tweet and clicked on that link.
This has an additional benefit in that because the tweet was so good, subconsciously we’ll make a little note about the user (particularly their name and avatar) and are more likely to notice them the next time they update. This attention will rise exponentially if their tweets maintain a consistent quality.
Likewise, if the quality of updates dips too sharply or wanders too far off-course, we’ll start to pay less attention, and in severe cases this can lead to a total tune-out and unfollowing. Hence, while being occasionally excellent is better than nothing, beingconsistently excellent is better than everything.
3. Sell The Headline (In A Non-Salesman Way)
People need a really good reason to click on your link. Remember, at any given time (and in almost any Twitter client) the reader is faced with a number of choices to make – there might be as many as a dozen different tweets on their screen, and a lot more if they’re using columns or groups.
And things move fast – one or two refreshes later, and you could be long gone.
So, even if you’ve been consistently excellent for tweet after tweet and dear reader comes straight to you, your job is not done. They still need a reason to click, which means your copy has to sell that link.
The trick is you have to do this in a way that makes it seem like you’re doing something else. People don’t really like to think they’re being sold to, especially in social media.
Let’s call it unselling.
It goes without saying that ‘click here to buy my stuff’ should only be used if your intention is to be completely ironic or you don’t actually care about people visiting your site.
Learn the difference between selling the link and selling the content – the content is what will sell your product or idea, but nobody is going to care about any of that unless you’ve first sold them the reason to read it. You might have discovered the cure for cancer, but nobody is going to care if you link it next to ‘This is cool.’
The reason can be number of different things. Promises work extremely well, but only if you actually deliver. Lie to people enough and it doesn’t matter how good your headline copy is. Honesty is essentially your best policy, but that doesn’t mean you can’t give it a fresh coat of paint with a little spin and reverse psychology.
It’s worth noting that superbly-written headline copy can often generate immediate retweets, even if it’s obvious the other party didn’t actually read the content, or because they trust and believe in you enough to make the (hopefully safe) assumption that you’re going to deliver the goods.
A word on linking to website content that is not your own – don’t be afraid to rewrite the headlines of others. Most of the time these are formatted to appease a single platform or marketplace, and won’t work as well on Twitter. Other times they just suck, plain and simple. If you can do it better, do it better. Nobody is going to object if you’re sending them solid traffic.
4. Use Correct (And Acceptable) Punctuation
Here’s the thing: I’ve never met anybody who was offended or put off when they read something that paid attention to the correct use of punctuation. The opposite is not true – many people (enormous numbers if you use the internet as a gauge) feel that, rightly or wrongly, missing or an incorrect use of punctuation reflects poorly on the writer.
This is certainly true when it comes to first impressions.
Use full stops and commas. Put your apostrophes in the right place. Use speech marks and parentheses.
Don’t end every sentence with an exclamation mark. A simple hyphen can often be the difference between a real word and one that doesn’t exist.
It can help to read your tweet out loud before you submit it. Are the pauses in the right place? We still need to breathe, even at 140 characters (or less).
Studies have shown that retweets contain more punctuation than normal tweets, even ignoring the colon that is automatically inserted by most Twitter clients (i.e., RT @).
Everything, that is, except semi-colons. I love the semi-colon, which is an underused and misunderstood little fellow at the best of times, but much as it pains me I feel it wise to leave them out of my tweets. It’s all about the little sacrifices.
5. Accept Nothing Less Than Flawless Grammar And Perfect Spelling
If you’re a bad speller, or struggle with grammar, consider writing your tweets in your favourite Word processor first. This might seem unnecessary, or even patronising, but let me just echo the sentiments above – people will judge you on how you write, and how you spell, and this will have a direct impact on whether your links are clicked and your updates retweeted.
A quick checklist for every tweet:
- Always start with a capital letter
- Always use a capital letter with each new sentence (and you only need one space after the full stop)
- Learn the difference between your and you’re, its and it’s and there, their and they’re
- Capital letters make it LOOK LIKE YOU’RE SHOUTING
- Avoid text-speak at all costs. Far better to take an extra minute or two to elegantly craft your message and link into the desired 140 characters than it is to resort to writing like somebody who dropped out of high school (and then banged their head)
Don’t look to celebrities for guidance here. Many of them break most of these rules, most of the time. It doesn’t matter for them, because they’re celebrities. The rules don’t apply. They’re going to get tons of attention and retweets no matter what they do. The same goes for lots of power-users and long-established Twitter veterans.
It’s different for the rest of us. Remember: be consistently excellent. You cannot afford to be anything less.
6. Observe The Magic Retweet Number
The magic retweet number is the total number of characters you need to leave blank at the end of every tweet to ensure maximum retweetability.
Over time, I have given considerable thought to this figure and continue to refine and perfect it. Currently, the magic retweet number stands at twenty-five. Which means your copy, plus link, should ideally be 115 characters or less.
This is a rule that you will need to break from time to time. Certainly, you should not sacrifice a really quality piece of copy to squeeze your tweet under that ceiling. And Twitter’s internal retweet mechanism has somewhat decreased the need to be so mindful of retweet space.
But if you never any room for others to share your message with their network, chances are that most of the time they either won’t make the effort, or that perfect piece of copy you wrote will be bastardised and lost to the horror of txt spk. Guess what – as it’s a retweet, now everybody thinks you wrote it like that. Welcome to your legacy.
7. Shorten All Links With Bit.ly (And Nothing Else)
This chart says it all.
If you’re using anything other than bit.ly to shorten your links – certainly if you’re using TinyURL – you’re actually hurting your brand. Bit.ly is Twitter’s URL shortener of choice and that recommendation, plus the stats and convenience that bit.ly provides, make it nothing less than essential for those looking to get their content re-shared.
Tip: the bit.ly sidebar is super-convenient.
Conclusion
Twitter is supposed to be fun, and doing everything by the book, or in a very methodical or rule-driven way, can sometimes make it seem just a little bit too much like hard work.
However, if you really want to succeed on the network, then you’re going to have to put in that little bit of extra effort. If you want to be consistently excellent then I’m afraid you will have to work hard – at least until it becomes second-nature. Few people are naturally wonderful, certainly all of the time.
Trust me: it’s worth the sweat. Once you see the benefits that great headline copy, can’t miss unselling techniques and first-class grammar and punctuation can make to your Twitter presence and impact – as well as your website traffic, and sales – you’ll never again settle for anything less than the perfect tweet.
If you enjoyed this post, here's some cool things you can do to give a little back:
- Follow @Sheamus on Twitter
- Like the Twittercism page on Facebook
- Share this article on one of these fine networks:
---------------
Now how to build the followers! Thanks to http://www.jamiefaidley.com for the great info on how to build followers on Twitter. I started a Twitter account last night and 24 hours later have 250+ following me just because of what is said about –so follow this advice if you are looking to build a twitter community of your own!
One thing that I really like about using Twitter as a marketing tool over blogging or even newsletters is how easy it is to build a large following. Of course, it isn't nearly as easy to make money from these followers so don't just disregard your traditional marketing tools because you have a lot of followers on Twitter. If you are new to the platform or your numbers have been stagnant then hopefully this post will show you how to get more followers on Twitter.
Find People to Follow
Friends: Start off by finding the people that you already know, this way you can build up some decent numbers before using any additional tactics, which will help because there is a landslide effect on Twitter which shows the more people that are already following you the more that will start to do so. (I'm assuming of course that your friends will follow you back, I mean they are your friends right?)
People with the Same Interests: You want to search for people who share the same interests as you, for example if you like sports then follow sports news services, major blogs, etc.
Industry Leaders: Find the key people in your industry and follow the same people they are, since chances are you will be interested in them as well.
Suggester Tools: Twitter's suggestion tool will help you find other people to follow.
Pace Yourself: Don't go out and follow 1,000 people over the next hour. Besides the fact that you look spammy just for doing this, when people come to your page they will see that you are following a massive number, but not being followed by nearly as many. To them this must mean that you are not popular in relation to the people you are following. Other Twitter users are normally pretty quick to follow you if you are following them, so add a batch, wait it out, then add another. Rinse and repeat this process over time and you'll start to accumulate a following. Just make sure you have a fairly balanced follower/following ratio. It also stands to reason that you should not use a script or bot to add followers because this is spammy and could get you banned from the system.
Follow People Back
The whole point of Twitter is to build relationships with other people, after all it is a socialmedia, so follow people back who follow you. As you start to get more popular on Twitter you will find that more and more people will start following you that you have never heard of before. If you follow every one of them back, you can lose track of the people that you actually signed up to follow. This is why you should probably have one account that you use for business and marketing that you strive for popularity and another you use just to follow the select few people you want to hear from. If you want to automatically follow people who follow you, sign up for TweetLater.
Be a Person
Seems obvious, right? I mean you are reading this article. Well, let's make sure that you are letting the Twitter universe know by going over the details on what I mean exactly by "be a person."
- Use a picture for an avatar - Show off your face and people will relate your tweets to you. A real picture for an avatar translates into you sharing real life experiences. Some people use a company or site logo to help with branding, but this isn't as personal and can cost you followers, but is better than nothing. If you just have the default image up then you can't be too serious about Twitter so why would anyone want to follow you?
- Name - You also want to have a real name and not just your company name.
- Details - Post a description or biography of yourself to give your account some personality.
- Add a link to your homepage - You want to let people know what you are about and what kind of information you will be providing, how else are they going to decide whether you are worth following or not? Besides, how are they going to visit your site if you don't provide a link and of course you want to increase your traffic numbers!
Again, this all adds up to showing that you are a real person and not spammer JohnDoe1212 or an evil corporate empire!
Tweet!
If your newest tweet was weeks ago then why would someone want to follow you? If you aren't updating your account then you must not be committed and are probably inactive. People want to know what you are currently doing or working on, but keep the noise to a minimum and don't spam everyone on your list. If you tweet more than 20 times per day you are clogging up my page and I will probably unfollow you. You also want your tweets to add value for your followers and contribute something to community, but they should also be fun so you don't bore your followers into ignoring you, or worse, unfollowing you! Great tweets on a consistent basis will not only help you to grow your following but also will get people to become more interested in what you are doing, thus driving traffic to your actual site.
Promote Yourself
There are several ways to promote yourself to increase your Twitter following. If you already have a blog then simply write a post about Twitter and add a link to your account in the article. If you have a newsletter send out a blast to your subscribers about how they can also follow you on Twitter. TwitterCounter has a chiclet that lets you show off how many followers that you currently have. Put your Twitter link in the signature of your emails or forum posts. You can even add cool buttons from TwitButtons or Twitter Buttons to spruce up your site a little bit.
-------------------------
Remember, if this all seems to much, Simply Seniors Computer Tutor can help! Simply Seniors Computer Tutor is the premier technical assistant for seniors! Not only do they offer classes at various locations throughout Brevard, they offer one on one in home services, virus clean up, repairs, pick up and delivery, new computer set up and specialty projects such as photo recoloring, digital photo archiving and much more. Simply Seniors Computer Tutors are Florida and Brevard County background checked, arrive in identifiable uniform, with company ID, additionally, UNLIKE the 'average guy' posting on CL, our company is licensed, insured and certified to work on your computer. KNOW YOUR COMPUTER TECHNICIAN do not allow just anyone into your very personal data and information or your home! Simply Seniors Computer Tutor understands seniors have unique learning abilities and we have spent the last 10 years researching the BEST methods for computer training and senior citizens. Stop struggling to use your PC or stop your parents constant phone calls asking "how do I..." Call Simply Seniors Computer Tutor today at 321-431-3866
www.ComputerTutorHelp.Us











 Better still, by building an
Better still, by building an