You never know with FREE software and even some paid for software – that is why it is always best to be careful and know what you are downloading and read the screens as they pass by. Today’s blog was first posted through Kim Kamando then through a local group I work with, the Space Coast PC Users Group. It’s worth passing along to anyone you know with a PC (that may be a little new to this stuff) :-). Remember when it comes to the Computer Health needs of Brevard’s Senior Citizens –look no further than Computer Tutor! 321-431-3866 and online at www.ComputerTutorHelp.Us
“ Many free software programs install browser toolbars and other programs. These may send your data to a third party. In many cases, they won't add anything to the Web browsing experience.
Programs may also change your file associations. This is a particular concern with media programs. Your files won't automatically open in your preferred program when you double-click them. Of course, you'll also find programs that install shortcuts on the desktop and system tray. Others plant toolbars in your Web browser.
Be sure to read the screens when installing software. I know, it's not fun. Uncheck any options for modifying files, installing add-on toolbars and other options that seem wrong. They probably are.”
Computer Tutor wants to take it a step further and show you the screen shots or commonly missed ‘malware’ or toolbars that come with software we like to download such as AVG FRee, CCleaner, and other great malware cleaning tools (with usefulness comes a price) what did you expect for free? OF Course they are going to try to slip something by you.
In this example you will see many different options, such as where the icon should be placed once the program is installed. Another option is to add the Yahoo tool bar. Not a necessary feature of the software and may be annoying to the person once it is installed. So watch for these little things. It will save you having to uninstall it in the future. 
Here is another commonly downloaded software AVG antivirus: In this case not only is your IE home page changed a tool bar is also added to the IE screen.
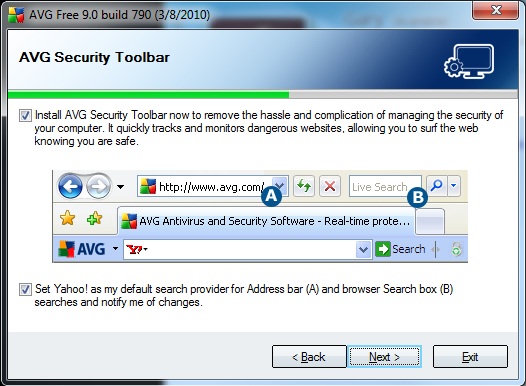
I use and highly recommend each of the software's shown here but they do come with some attachments that you have to watch out for. If you pay attention to what you are downloading and watch and read the screens presented to you during the install process you should be able to take well educated decisions about what your are installing.
I hope you have found this information helpful. If you have learned something please pass this blog around to your friends.
Thanks!
Stacey Kile
Computer Tutor of Melbourne Florida 321-431-3866




